Education
Critical Differences Between CMMC Level 2 Assessments and Other Compliance Audits

Compliance audits aren’t created equal, and anyone working toward a CMMC Level 2 Certification Assessment quickly realizes this. It’s not just another checklist—it’s a much deeper process built to match national defense standards. Understanding what separates this level from a typical audit can help contractors prepare smarter, not harder.
Explicit Evidence Requirements Unique to CMMC Level 2
Standard audits often allow organizations to talk through their controls or provide basic documentation to prove compliance. In contrast, a CMMC Level 2 Assessment demands hard proof. Assessors want specific, traceable evidence for each security practice. That includes detailed configurations, screenshots with time stamps, and system logs that show a control has been in place over time—not just on the day of the audit.
This is one of the more demanding aspects highlighted in any solid CMMC assessment guide. Verbal confirmation doesn’t cut it. Organizations must walk into the assessment with a clear record of how each control is implemented, maintained, and monitored. This isn’t just policy on paper—it’s proof in action, tied directly to cybersecurity outcomes.
Continuous Security Monitoring Beyond Standard Audits
Traditional compliance checks often focus on a point in time. They ask, “Are you secure today?” CMMC Level 2 Certification Assessment flips that question into, “Have you stayed secure over time, and can you prove it?” This shift brings continuous monitoring into the spotlight, pushing organizations to maintain logs, alert systems, and updates that track threats as they emerge—not react after damage is done.
This ongoing scrutiny is what sets a CMMC Level 2 assessment apart. Instead of treating cybersecurity like a yearly box to tick, this process expects it to be woven into daily operations. Monitoring tools, incident response systems, and behavioral analytics become part of the required evidence. It’s a living audit, not a snapshot.
Defined Scoping Boundaries Distinct to CMMC Framework
One of the lesser-known aspects of a CMMC Certification Assessment is how tightly scoped it is. CMMC defines the exact boundaries of the systems handling Controlled Unclassified Information (CUI). Unlike broad audits that may assess entire networks or departments, this assessment isolates only the systems that interact with CUI—and the surrounding connected components that could affect security.
This defined boundary ensures that the assessment stays focused, but it also means organizations must be meticulous in identifying where CUI lives. A firewall misconfiguration or an unprotected endpoint within that boundary can lead to a compliance failure. The CMMC assessment guide stresses the importance of scoping correctly from day one, or risk gaps being discovered too late in the process.
Enhanced Artifact Collection Protocols in CMMC Evaluations
Think of artifacts as receipts for every cybersecurity promise made. While regular audits might ask for policies or occasional screenshots, CMMC Level 2 Certification Assessment goes deeper. It requires layered, repeatable evidence—config files, audit logs, training records, screenshots, and even user access histories. And those items need to align with the control’s intent and time frame.
Collecting and organizing these artifacts becomes a full-time effort in the lead-up to an assessment. Assessors won’t chase details—they’ll expect a clear system in place to retrieve evidence quickly and accurately. The better prepared an organization is with these records, the smoother the CMMC Level 2 Assessment will go. It’s about showing your system works under pressure—not just saying it does.
Rigorous Third-Party Oversight Specific to Level 2 Compliance
Here’s where the CMMC model really breaks from tradition: Level 2 requires assessment by an accredited third-party organization, not just an internal review. These C3PAOs follow strict procedures to evaluate compliance. Their findings must hold up under review from the DoD, which means the assessment process is layered with accountability and quality control.
The presence of a C3PAO changes the dynamic. There’s no room for friendly interpretation or loose ends. Each assessor brings consistency and structure to the audit, guided by the CMMC assessment guide. That level of rigor ensures fairness—but it also means preparation must be thorough, clear, and complete. It’s a high-stakes process, but one built for national trust.
Specialized Controls for Controlled Unclassified Information CUI
Handling CUI isn’t just another data responsibility—it’s treated as a national security matter. That’s why the CMMC Level 2 Assessment includes specific controls tailored to protecting this information. These controls go far beyond what general audits require, including strict encryption rules, access management, and physical safeguards.
The goal is to ensure CUI never ends up in the wrong hands—whether through system breach, employee error, or misconfigured storage. Organizations pursuing CMMC Level 2 Certification Assessment need to prove they’ve built walls around CUI, and that those walls are checked and reinforced regularly. It’s not just about digital protection but the full lifecycle of sensitive data.
Prescribed Self-Assessment Methodologies Unique to CMMC
Standard audits sometimes offer vague self-assessment guidelines. CMMC takes a different route. Even before bringing in a third-party assessor, organizations must follow specific self-assessment methods outlined in the CMMC assessment guide. These methods are not optional; they’re the warm-up before the real test.
The self-assessment for CMMC Level 2 isn’t about checking boxes. It’s a structured, documented process that shows an organization understands its security stance and has already taken steps to improve it. By aligning internal practices with CMMC guidance early, companies position themselves for a smoother certification journey—and fewer surprises when third-party eyes are watching.


 Travel2 years ago
Travel2 years agoPractical And Essential Car Interior Accessories To Add Comfort And Convenience To Your Drive

 Business2 years ago
Business2 years agoTop Reasons Why you Need to Consider Outsourcing Real Estate Photo Editing
 Business2 years ago
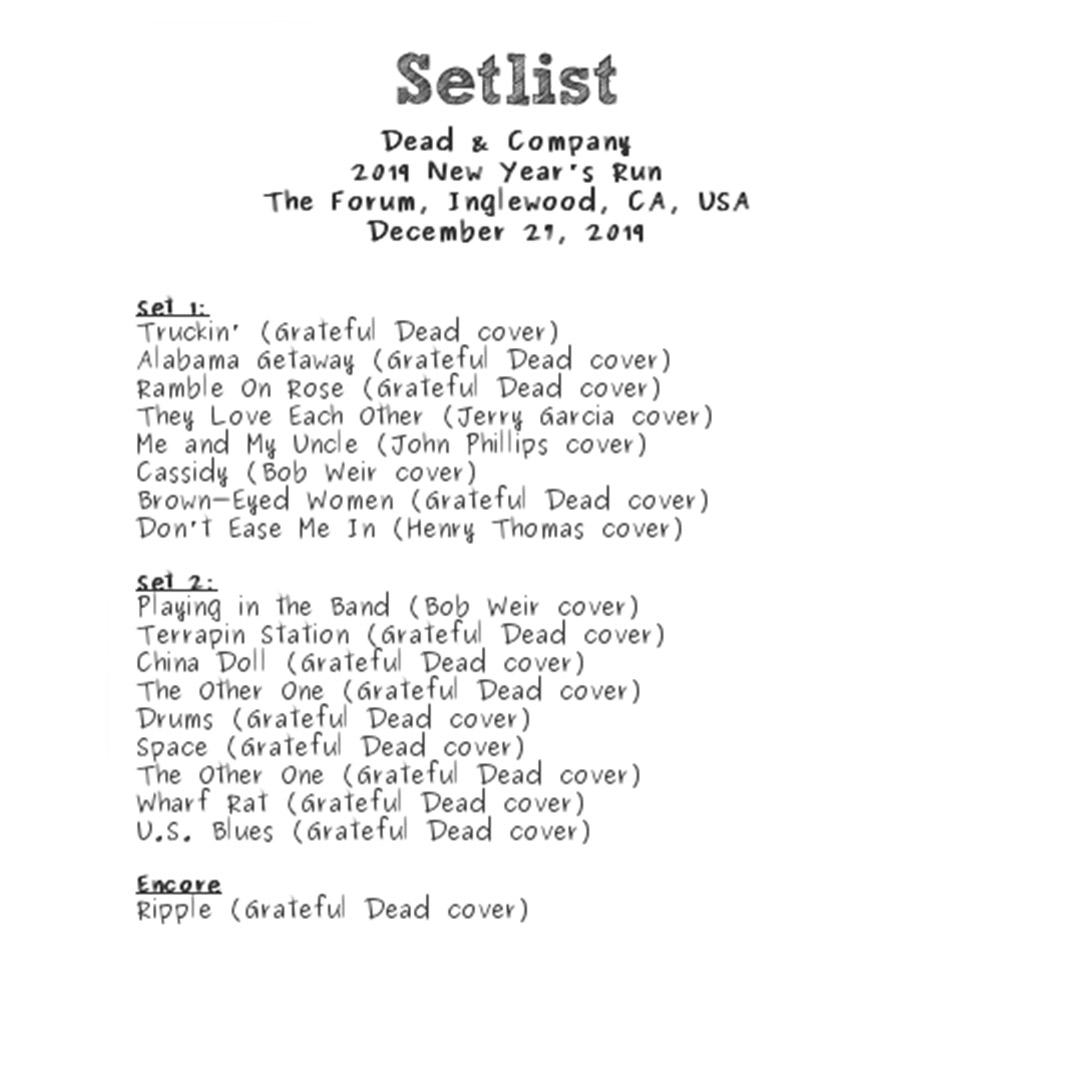
Business2 years agoDead And Co Setlist What They Played At The Gorge Amphitheatre

 Featured2 years ago
Featured2 years agoHow to Make a Sports Career in India

 Health2 years ago
Health2 years agoGarlic Is The Best Vegetable To Treat Heart Problems

 Sports2 years ago
Sports2 years agoHow to watch the ETSU game -What are the benefits of watching the ETSU game?

 Health2 years ago
Health2 years ago5 Reasons to Choose Turkey for Dental Treatments

 Travel2 years ago
Travel2 years agoSpectacular Hot Air Balloon Rides in Goa