Tech
The Benefits of Implementing Identity and Access Management Systems in Business Operations
Managing employee access to information and systems is vital for business operations. Identity and access management (IAM) systems help to protect company assets while improving productivity.
IAM uses digital identities to identify, authenticate and authorize users to access enterprise resources. The system also supports centralized administration and control.
Security
Identity and access management is an essential tool for business operations because it helps to protect the company from threats like data theft, malicious attacks, or data breaches. It ensures that only authorized users can access systems, databases, and information.
IAM allows organizations to establish privileged groups and assign access rights based on employees’ job functions. They can also modify privileges by using request and approval processes to change the access granted to individual employees.
The security benefits of IAM include reduced risk, meeting compliance requirements, and improved productivity. IAM also increases efficiency by reducing the need for IT professionals to manage user registrations and changes in access settings manually.
IAM systems can be implemented on-premises through a cloud-based or hybrid model. They offer a variety of authentication methods and support data governance functions, which can be used to monitor suspicious activity and report incidents.
Identity and access management also eliminates the need to remember multiple passwords, allowing for a seamless Single Sign-On (SSO) experience. Moreover, it provides strong multifactor authentication to reduce the risk of stolen credentials.
Efficiency
An identity and access management system can be a good solution for businesses looking to improve security and streamline operations. They can save time and money by reducing IT department tasks like password resets, unlocking accounts, and monitoring access logs for anomalies.
IAM systems can also help improve employee productivity by reducing the logins and passwords required for users to access their accounts and resources. These features can also help reduce security breaches and cybercrime.
In addition, identity and access management systems can be used to secure data by requiring users to provide multiple authentication factors, such as usernames, passwords, biometrics, or two-factor authentication. IAM systems can then compare these factors to records in a database to ensure that they match.
By automating the process, IAM can simplify user lifecycle processes such as new hire onboarding, internal transfers, and role changes. This can significantly improve processing times and reduce errors, reducing costs and increasing user satisfaction.
Compliance
Identity and access management is the process of defining roles, providing identity assurance through multifactor authentication, and managing permissions to resources within the enterprise. It helps organizations maintain security and compliance by limiting access to critical information and systems.
Increasingly stringent compliance regulations and data protection standards require that businesses have a clear picture of who has access to important company information and what they are doing with it. IAM solutions provide the visibility, controls, and audit trails necessary to meet these regulations.
IAM also makes it easier to meet privacy and security regulations like the General Data Protection Regulation (GDPR) in Europe, Health Insurance Portability and Accountability Act (HIPAA), Sarbanes-Oxley Act, and more. It also provides tools for verifying identities, detecting suspicious activity, and reporting incidents.
A well-implemented IAM solution is essential to any modern IT environment, especially in a digital business. Its benefits include security, productivity, efficiency, and flexibility, all of which help companies to achieve their goals.
Flexibility
Identity and access management systems help organizations secure digital identities and control user resource access. These tools can include single sign-on systems, two-factor authentication, and privileged access management.
IAM also helps companies meet data protection and compliance requirements, such as HIPAA and GDPR. It enables businesses to verify identities, monitor suspicious activity, and report incidents.
Authentication: IAM solutions can use multifactor authentication, adaptive authentication, and password/facial recognition to confirm users’ identities. These processes can consider location, time, and device, depending on the system.
Provisioning: IAM systems allow IT departments to provision user access based on roles and department-level policies automatically. This method significantly reduces the manual work required to define and enforce user access to resources.
IAM allows organizations to automate many manual tasks, allowing IT professionals to focus on non-automated projects requiring expertise and attention. This helps improve team members’ productivity and collaboration while reducing security risks.
Scalability
Identity and access management (IAM) is crucial to business operations. It helps manage user identities, enabling employees and contractors to access company information securely. It also allows companies to create data policies that prevent data loss and theft.
IAM solutions enable companies to manage and control user identities through various authentication methods, including passwords, one-time personal identification numbers (OTPs), biometric data, and other factors. These techniques ensure that only authorized users have access to corporate resources.
These methods are essential because they help protect corporate data’s integrity and security while increasing user productivity. They also allow businesses to demonstrate their compliance with regulatory standards like HIPAA and SOC 2.
As part of an IAM solution, organizations need to identify where digital identities live–in enterprise, cloud, or siloed systems–what they can access, and what job functions and processes they correspond to. These issues must be addressed top-down, focusing on aligning business processes, people, and technology. This helps to streamline user authentication procedures and reduce the complexity of implementing and maintaining IAM controls.

Tech
Modern AI Navigation: 3 innovative options for use

Machine learning and deep learning are integral to various industries. Ground transportation systems leverage predictive algorithms to optimize travel flows, forecast congestion, and enhance fuel efficiency. Now, these advancements are taking flight.
Significant strides in AI navigation are transitioning from research labs to mainstream applications, offering aeronautics enhanced reliability, safety, and efficiency.

AI-Powered Inertial Navigation for UAVs in GPS-Compromised Environments
In many UAV operations, GPS signals are crucial. However, these signals can be disrupted during natural disasters or military operations. Bavovna.ai, a graduate of the US Air Force Labs Mass Challenge acceleration program, is pioneering an AI-driven PNT navigation system for aerial, surface, and subsurface vehicles.
Dual-Use AI Navigation for UAV Drones
Bavovna’s inertial navigation system, designed for dual use, utilizes sensor fusion and pre-trained ML/DL algorithms to enable autonomous operations. With robust core electronics, the system withstands common electromagnetic warfare threats. It’s also a low-SWaP (Size, Weight, and Power) solution, making it ideal for UAV models and Class II aerial vehicles.
In trials, the Aurelia X6 Max multicopter operated autonomously without remote control, GPS, or other communications, gathered location intelligence, and returned to its starting point. Bavovna’s AI navigation system aims for a positioning error margin of just 0.5%, even on complex routes up to 30 miles (48 km). The team is expanding its use cases to include Signals Intelligence, mine detection, automatic target engagement, and security surveillance.
AI Copilots for Commercial Aviation
Modern aircraft are equipped with sophisticated autopilot systems to assist pilots in controlling altitude, course, thrust, and navigation. However, pilots can be overwhelmed by the numerous alerts and system interfaces demanding their attention. NASA estimates that pilots are distracted by 34 different activities, from communication to scanning for visual meteorological conditions (VMC) traffic, which can lead to human errors and potential dangers.
AI Airflow Traffic Management
The Air-Guardian project by MIT’s CSAIL seeks to improve the human-machine interface (HMI) of existing autopilot systems for safer operations. The AI system uses eye-tracking to detect pilot distraction and “saliency maps” to understand aircraft behavior.
Based on a continuous-depth neural network model, the copilot system can identify early risk signs and take control when necessary. During trials, the Air Guardian system reduced flight risks and improved navigation success.
Advanced Airflow Traffic Management to Alleviate Congestion
Unpredictable events like adverse weather can significantly impact air traffic, causing congestion in specific airspace sectors. This congestion affects all network participants, resulting in a cascade of delayed flights.
Co-funded by the European Union and led by Universita Ta Malta, the ASTRA project aims to predict air traffic congestion one hour in advance and suggest optimal paths for traffic controllers. The project, which stands for AI-enabled Tactical FMP Hotspot Prediction and Resolution, trains its prediction algorithm on historical data from EUROCONTROL (from 2019 onwards). The AI system provides prescriptive scenarios to optimize flow management positions, ensuring safety, efficiency, reduced fuel consumption, and minimal environmental impact.
AI holds immense potential in airborne navigation, and we anticipate further innovations in sensor fusion, AI-powered PNT, and aerial traffic management in the coming years.
Tech
Boost Your Telegram Channel Promotion with KYG’s Services

Telegram channels are powerful tools for businesses aiming to enhance brand awareness, share valuable content, build active communities, improve customer relationships, and boost sales. However, effective telegram promotion and management requires strategic efforts. This article explores how KYG’s services can support your Telegram channel promotion, leveraging advanced tools and strategies to maximize engagement and growth.

Services for Telegram Channel Promotion
Creating engaging content is critical for any social media platform. On Telegram, diverse content types such as text, media, and polls can captivate your audience. KYG’s services can assist in developing a content strategy that resonates with your target audience. With tools to set clear objectives and KPIs, KYG ensures you monitor key metrics and adjust your strategy based on performance and feedback.
Cross-Promotion Tactics
Expanding your reach through cross-promotion is vital. KYG supports cross-promotion efforts by providing insights into the most effective platforms for your audience. Whether you’re leveraging other social media channels or partnering with similar communities, KYG’s analytics help identify and optimize these opportunities, ensuring you attract engaged and interested users.
Influencer Partnerships
Influencer marketing is indispensable for boosting engagement and communication. KYG’s platform aids in identifying influencers who align with your brand values and target audience. By facilitating clear collaboration proposals and tracking campaign results, KYG ensures that your influencer partnerships are both effective and measurable, driving more users to your Telegram channel.
Exclusive Offers and Contests
Offering exclusive content and running contests are proven methods to boost engagement. KYG can streamline the process of advertising these offers across various platforms, ensuring maximum visibility. Additionally, KYG’s analytics tools help monitor the effectiveness of these campaigns, providing valuable insights for future strategies.
Consistent Communication and Engagement
Maintaining an active community requires consistent engagement. KYG’s community management tools make it easier to plan and track communication efforts. By providing comprehensive analytics and personalized recommendations, KYG helps ensure that your Telegram channel remains vibrant and engaging. Responding to comments, rewarding active members, and monitoring community health are all simplified with KYG.
Why Choose Know Your Group
KYG offers a comprehensive suite of tools and services designed to support effective Telegram channel promotion. With KYG, you get:
- Advanced Analytics: Monitor engagement, growth, and performance with precision.
- Customizable Community Portals: Tailor your community space to reflect your brand’s identity.
- Streamlined Onboarding: Easily integrate new members into your community.
- Monetization Tools: Turn your engagement into revenue with various monetization strategies.
- Expert Support: Benefit from personalized recommendations and strategic growth insights.
Know Your Group ensures your Telegram channel thrives, driving engagement and achieving your business goals.
FAQs
What is the best way to create engaging content for a Telegram channel?
Utilize diverse content types like text, media, and polls, and tailor your content to your audience’s interests and needs. KYG’s tools can help set clear objectives and track content performance to make necessary adjustments.
How can KYG help maintain consistent communication on Telegram?
KYG’s tools streamline communication planning and tracking, making it easier to engage with your community regularly. Their analytics provide insights to improve engagement strategies continuously.
What makes KYG a good choice for Telegram channel promotion?
KYG offers a comprehensive suite of tools for community management, including content strategy, cross-promotion, influencer partnerships, and engagement tracking, all tailored to help your Telegram channel succeed.
Tech
Coingama Exchange Review
Coingama is emerging as a premier cryptocurrency exchange platform, designed to cater to both beginner and seasoned traders. With its user-friendly interface, advanced security measures, and comprehensive trading tools, Coingama aims to provide a seamless and secure trading experience. This review delves into the various features and benefits that make Coingama a standout choice in the crowded cryptocurrency exchange market.
User Experience: One of the defining features of Coingama is its intuitive and easy-to-navigate interface. The platform is designed with user experience in mind, making it accessible even for those new to cryptocurrency trading. The registration process is streamlined, allowing users to set up their accounts quickly and start trading without unnecessary delays. The dashboard is well-organized, providing users with all the necessary tools and information at their fingertips. Additionally, Coingama offers a mobile application, enabling users to trade on-the-go with the same level of efficiency and security as the desktop version.
Security Measures: Security is a paramount concern for any cryptocurrency exchange, and Coingama excels in this area. The platform employs a range of advanced security measures to protect users’ funds and personal information. These include two-factor authentication (2FA), encryption, and the use of cold storage for the majority of users’ assets, which significantly reduces the risk of hacking. Coingama also conducts regular security audits and updates to ensure that its security protocols remain robust and up-to-date. Users can trade with confidence, knowing that their assets are safeguarded by some of the most advanced security measures in the industry.
Trading Features and Tools: Coingama offers a comprehensive suite of trading features that cater to a wide range of traders. The platform supports numerous trading pairs, including major cryptocurrencies such as Bitcoin, Ethereum, and Litecoin, as well as various altcoins. This wide selection allows traders to diversify their portfolios and take advantage of different market opportunities. Coingama also provides advanced trading tools, including real-time charts, technical indicators, and market analysis, which help users make informed trading decisions. The platform’s trading engine is designed for high performance, ensuring fast and reliable execution of trades even during periods of high market volatility.
Liquidity and Fees: Liquidity is a crucial factor for any exchange, and Coingama ensures ample liquidity across all trading pairs, allowing for smooth and efficient trading. The platform has partnered with several liquidity providers to maintain tight spreads and minimize slippage. When it comes to fees, Coingama is competitive, offering a transparent fee structure with no hidden charges. Trading fees are kept low to attract more users, and there are various incentives and promotions available that further reduce the cost of trading on the platform.
Customer Support: Reliable customer support is essential for any trading platform, and https://coingama.com/ excels in this area as well. The exchange offers 24/7 customer support through multiple channels, including live chat, email, and a comprehensive FAQ section. The support team is responsive, knowledgeable, and dedicated to resolving any issues that users may encounter. This level of support ensures that users can trade with confidence, knowing that assistance is readily available whenever needed.
Educational Resources: Understanding the importance of education in trading, Coingama provides a wealth of educational resources for its users. The platform offers tutorials, webinars, and articles that cover various aspects of cryptocurrency trading, from basic concepts to advanced strategies. These resources are designed to help traders enhance their knowledge and improve their trading skills, making Coingama an excellent choice for both learning and trading.
Conclusion: In conclusion, Coingama is a reliable and efficient cryptocurrency exchange that offers a comprehensive trading environment. Its user-friendly interface, robust security measures, advanced trading tools, ample liquidity, competitive fees, and excellent customer support make it an attractive option for traders of all levels. Whether you are just starting out in the world of cryptocurrency trading or are an experienced trader looking for a dependable platform, Coingama provides the features and support needed to succeed. With its commitment to security, innovation, and user satisfaction, Coingama is well-positioned to become a leading player in the cryptocurrency exchange market.

 Others10 months ago
Others10 months agoDavid T Bolno: Why Giving Back To The Community Is So Crucial

 Travel10 months ago
Travel10 months agoPractical And Essential Car Interior Accessories To Add Comfort And Convenience To Your Drive

 Travel10 months ago
Travel10 months agoBusiness Visa for CANADA

 Business10 months ago
Business10 months agoTop Reasons Why you Need to Consider Outsourcing Real Estate Photo Editing

 Health10 months ago
Health10 months agoGarlic Is The Best Vegetable To Treat Heart Problems

 Fashion10 months ago
Fashion10 months agoTips For Choosing The Right For Engagement Diamond Rings
 Business10 months ago
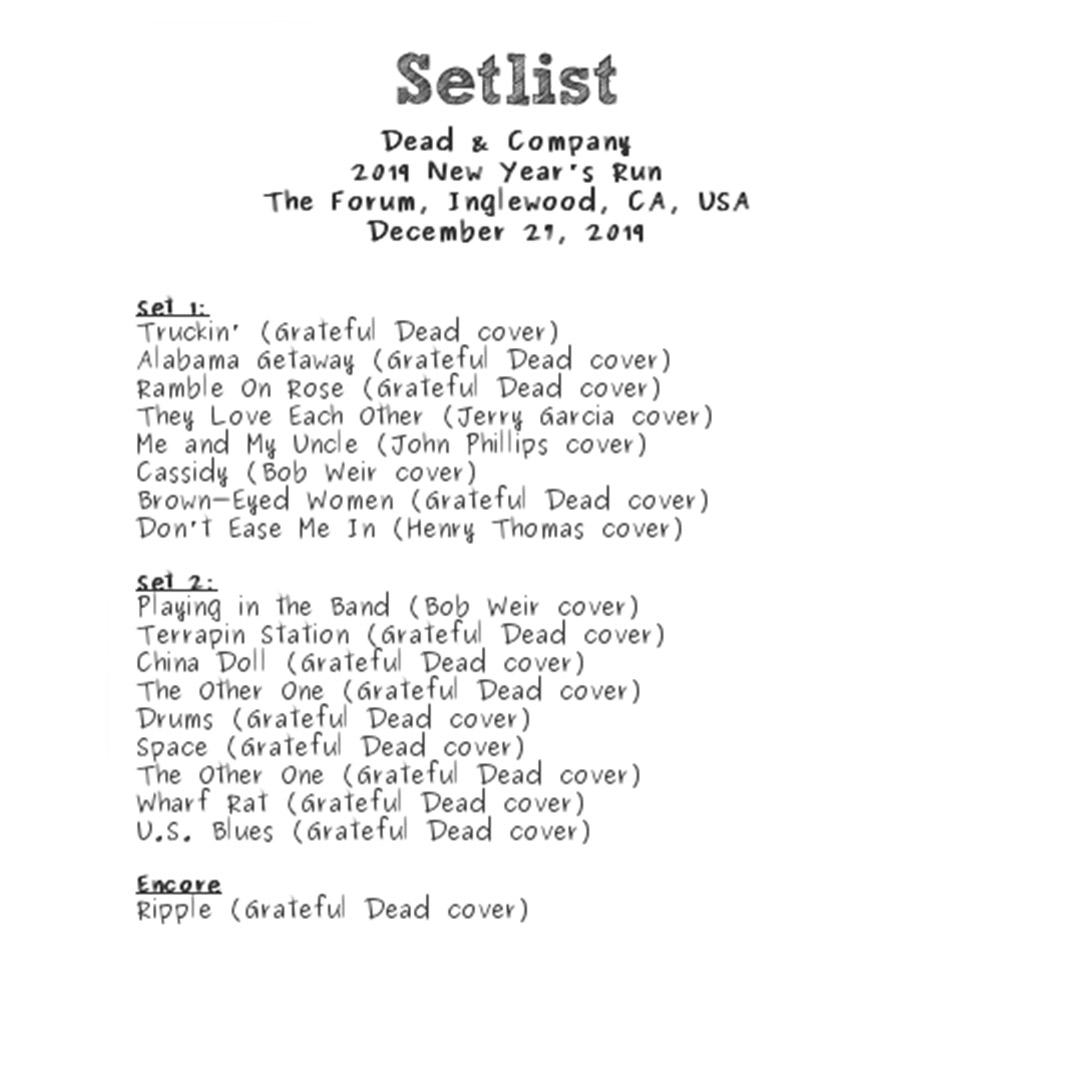
Business10 months agoDead And Co Setlist What They Played At The Gorge Amphitheatre

 Tech10 months ago
Tech10 months agoThe Best Way to Never Get Lost: Buy Wayfinding Signs!